
How can I understand the IoT threat?
And what does Shodan have to do with it?
This guide explains everything you need to know about this topic.
Let’s get started!
What is IoT?
“Internet of Things” is another great buzzword that every 2nd startup is advertising with today.
Any technical device that is connected to the internet can call itself an IoT device.
In the past, internet participants were limited to closets full of servers and grey desktop computers sitting under every desk in the office.
Today, internet-connected devices have continued to shrink and no longer need a cable (WLAN). The media often associates IoT devices with …
- Coffee machines with app control
- Ceiling lighting with intelligent control
- Heating systems that heat depending on presence
Industry likes to use internet-connected devices because it allows you to monitor and optimize production lines. Every motor, sensor or machine uses internet connectivity to communicate throughput, product quality or more.
What are the issues with IoT?
Like any technological innovation, IoT comes with a big problem:
Poor patchability
Employee computers are “easy” to update because they are uniform and there is management software.
IoT devices are often produced so cheaply that they cannot load an update because the memory is too small. IoT devices perform non-critical, simple activities, but can cause great damage if criminals take them over.
What is a DDoS?
Distributed Denial of Service – One for all, and all for one criminal! The 1000+ microcomputers can create a storm of requests that can disable well-known online shops. These bombard systems with unnecessary requests so that they can no longer withstand the load.

What is Shodan?
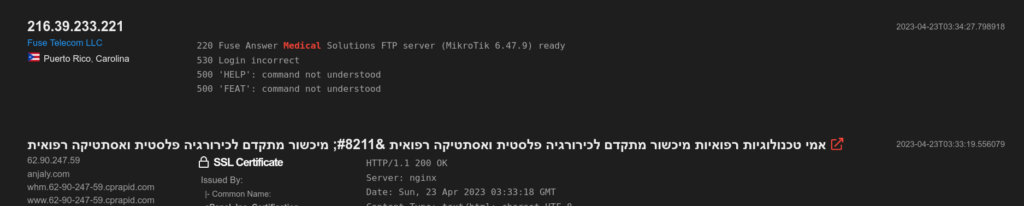
Shodan is a search engine that scans the internet for devices. The system works like a normal search engine. You can make an entry: e.g. Netgear router. Shodan will then list all systems that are very likely to be a Netgear router that are publicly available on the internet.
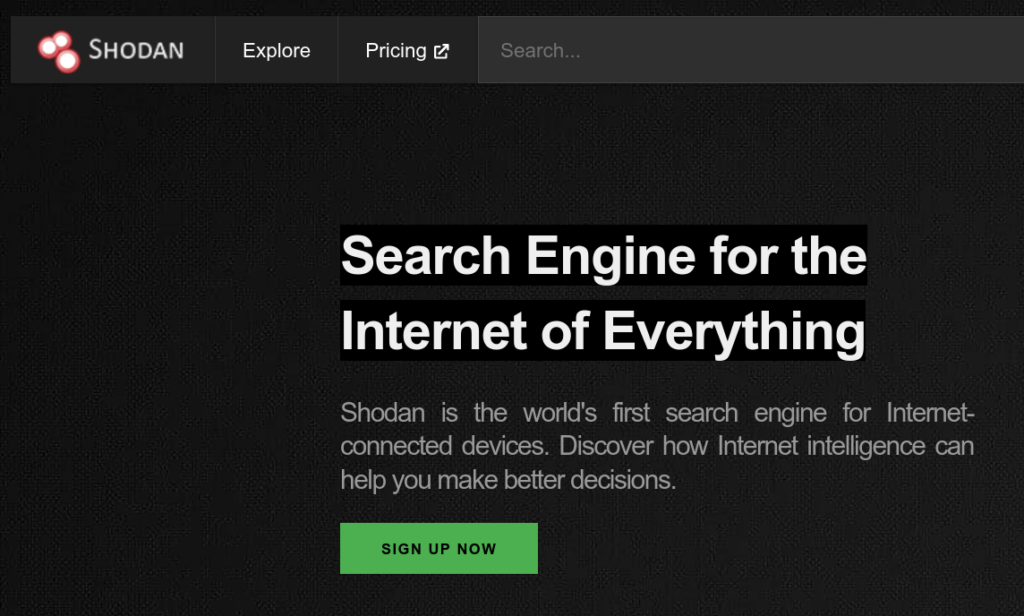
The search engine allows deep insights.
Each machine responds to Shodan in its own product-specific way, allowing Shodan to store the type of device. Even a screenshot of remote desktop transmission can be displayed by the search engine.
Some of the queries take much longer than Google’s because Google can structure the data (text) better than the mishmash Shodan finds on the internet. Shodan indexes everything that Google does not want to index or indexes unintentionally.
These systems are neglected computers, private insecure home automations, network devices in large companies or unprotected databases that expose all their knowledge.
The IPv4 address space is so limited that Shodan can usually find a device with a randomly generated IP. The device includes Shodan in its index and checks from time to time if anything has changed.
How do I use Shodan?
Go to: https://www.shodan.io/
1. First enter a product name (hardware or software) – or any term you want to search for
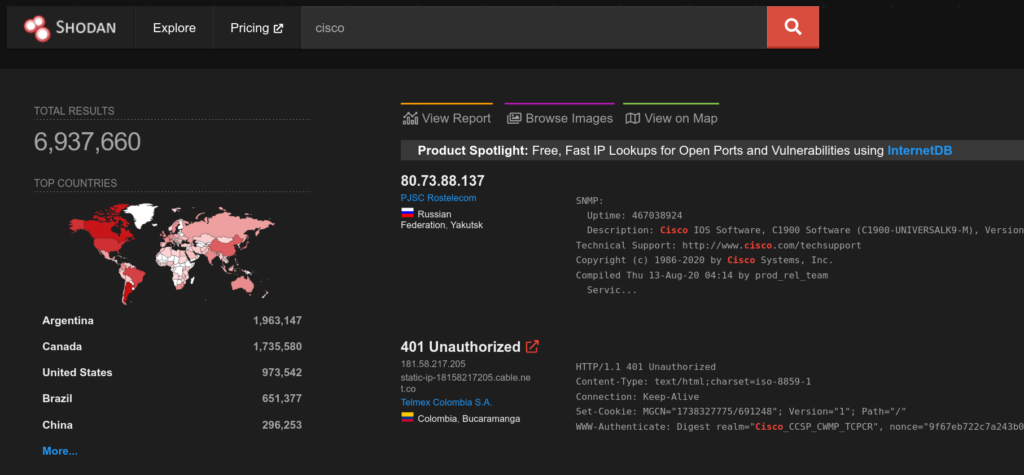
2. Filter on the right side by country. Which systems in the world are I most interested in?
3. Which organizations publishes the system? Most of the time you will find Amazon, Microsoft and Google in the top positions because they are cloud providers themselves. In their address space are their customers who publish content.
4. Filter by other criteria, such as the operating system. Often the software is patched, but not the foundation.
If you want to get more information, you have to scan the machine yourself with nmap. Shodan is good for a quick exploration, but for an actual detailed analysis you have to investigate the given IP further
How can I avoid showing up on Shodan?
Change default passwords
The big problem with many IoT devices is that they come from the factory with default passwords that are known to the world public.
Every buyer of this product connects a device to their internal network, which at the time of purchase is already a gateway for criminals. Therefore, you should inform yourself how (if) you can change the password of SSH, HTTP, Tomcat, Telnet and other services.
Update the software / firmware
Security bugs are the bread and butter of criminals.
Within minutes, criminals start attacking machines when a new exploit becomes known. The manufacturer delivers many IoT devices with a “working” firmware, which is already old at the beginning of the sale. Cheap devices cannot technically update because the chip is not rewritable or there is no space available for the update.
Nevertheless, you should not simply connect devices to your network that you will never be able to patch, or only with great difficulty.
Not everything needs internet
You are not obliged by law to connect all your devices to the internet. Your smart coffee machine doesn’t have to interact with the Netflix server or check the news.
Many IoT devices provide information that you use in the local network and an internet export is not necessary. If you do, you can run the system through a secure device (proxy) that you always patch to the latest version.
Harden your systems
Hacking is an art.
So is resisting a hack!
Computer scientists call securing systems “hardening”. Like the blade of a sword, more processing is needed to make a better, stronger and more robust product.
Swap or change ports
In an operating system, the various programmes and services hide behind known port numbers.
Up to port number 1023, we are talking about system ports that use the most important and popular services, such as HTTP (80) for websites or SSH (22) for secure transmission of commands. Between port 1024 and 49151 you can define yourself which software runs there, and between port 49152 and 65535 the client programs start services themselves.
Whenever possible, you should pack attackable ports such as SSH on other ports. You can continue to use the service, while criminals initially assume that your device is not accessible with SSH.
Consider secure architectures at the beginning
What are solutions for IoT security?
You can buy a smart lamp for €8 at the DIY store and easily build a smart home. This approach does not promote your IT security; you have to think carefully about which systems you bring into your house.
A good strategy is to pack sensitive hosts of the IoT devices into an extra subnet, e.g. 2.4 GHz WLAN, and to prevent them from communicating with each other. Furthermore, you can connect them to a “secure” control centre, which you can easily patch. This control centre forwards your commands from the home network or the Internet.
