How to Bypass a Paywall?
Here’s your guide for many of your favourite websites!
Let’s get started!
What is a paywall?
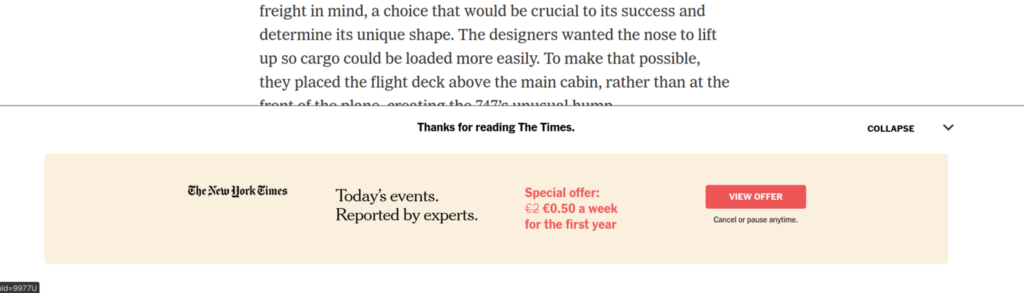
Website operators use paywalls to allow only paying customers access to content. Often the content can be found on their website or in your search engine, but the website only partially displays the content. To access the content, you have to sign a purchase or rental contract that can bind you for up to two years under German law.
Why do companies use them?
Companies want to make all paid content and the introduction available to everyone so that potential customers notice it. Everyone knows this from the real world too.

- In drugstores, you can sniff a sample of the fragrance to make a “rational” decision
- Fresh food counters offer (big) kids a slice of sample X or Y
- The first 10-min ride on an e-scooter is free of charge
Limitation in the digital world
The digital world can set sample limits even more easily. Samples are available online for all to see, showing 200-word text, a 30-second video or a short audio clip. These texts serve as bait for these companies to persuade them to sign up for a large subscription.
A search engine can only show content to the user if it is accessible from the internet without a password. In the best case, the Google crawler has to evaluate the entire article so that the algorithms rate it well. The bot categorizes too short, content-less web pages further down.
How does the hack work?
Not every paywall is built the same way, but many websites use insecure, simple plug-ins with which they hope to achieve quick success.
Often, these are CSS-style operations that simply cover up the text. The browser user has full control over all content and presentation within his browser.
If you want the text of your daily magazine to appear pink now, you can change it in 2 minutes. You can implement a CSS manipulation of any web page in real time.
Is paywall circumvention legal?
Data that is publicly accessible on the internet, which does not have any kind of access protection (even very bad ones) can first be accessed legally.
Depending on the content, German copyright law may prohibit you from viewing (rights of use). This must be decided on a situational basis. In general, publicly available content should be legally retrievable on the net.
The 4 best tools for bypassing paywalls
The all-rounder – Bypass Paywalls Clean
This extension is able to bypass the paywall of many German newspapers. This list can change daily, depending on whether the website operator uses a proper paywall. The magic of the plugin takes place on the client side.
Everyone gets the textual basis transferred to their device in full, but not displayed in full. Because you can change pretty much every aspect of the local display, you can have every article displayed in full length.
You can install the plugin for Firefox or Chrome.
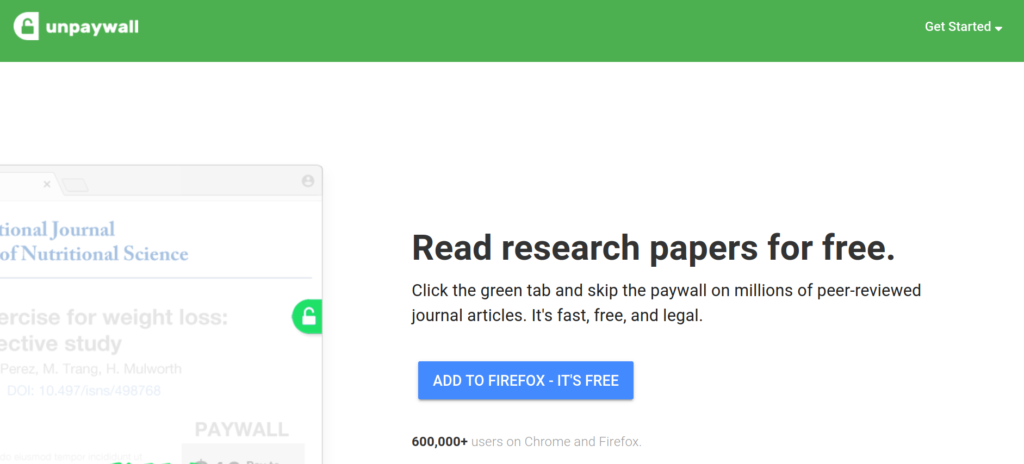
Interesting for students and researchers – Unpay
The add-on “Unpay” does the same job. This software focuses on scientific documents that require compulsory registration.
The add-on prevents website operators from collecting too many e-mail addresses for a service that they have not provided themselves.
Steffen Lippke
Bypassing means reducing – JavaScript off
A similar method to circumvent a paywall is to switch off JavaScript. JavaScript is a client-side programming language that makes web pages interactive in the browser. The browser does not have to reload every time, but can change with HTML, CSS and JavaScript.
The nastier form of the paywall – geo-blocking
Geo-blocking uses a similar approach to a paywall.
Effectively, both methods prevent the user from viewing the content. Geo-blocking aims to exclude people of a certain region from access. The user can use a Virtual Private Network to fake their location. The website operator thinks that the user is in a different country than intended.
Which paywall is secure?
Paywalls can only be secure if the entire article is not transmitted. But in order for authorized users to see them, we need an authentication concept.
A database stores the login data of the users and monitors the duration of the subscriptions. Users have to log in with a password, for example (authentication):
Secure Paywall One-Time-One
This form of paywall is much more complex because it involves a rat’s tail of tasks:
- A proper implementation of authentication is necessary. All passwords must be securely encrypted (see hash).
- Users like to forget passwords. The user should be able to reset his password by mail. The operator still needs a mail server for this.
- The underestimated GDPR requirements entail further tasks. Users can extend a data disclosure or submit a deletion request
- The operator must consider the hidden security requirements. The admins must, for example, keep the systems up to date (patching).
No one wants to implement all these requirements voluntarily. It’s much easier to just install a WordPress plugin that half-does the job:
What is the best form of authentication?
There is no perfect form of authentication. The paywall is only as secure as the authentication method you choose. Each form has advantages and disadvantages. It makes much more sense to combine different types:
- Knowledge: Any form of knowledge e.g. a password or pass phrase will help authenticate a person.
- Being: Biometric features such as fingerprints or faces are different for each person. Modern software and camera technology recognizes legitimate persons. The systems reject strangers and criminals because the systems themselves reject photography.
- Possession: One-time passwords are good for authenticating people. These can be carried by the devices. These include one time passwords, RSA tokens and smart cards.
