
You need a secure storage?
You’ve often heard the term, but you can’t do anything with it.
I’ll show you all the ways you can store content securely at low cost.
Let’s get started!
What does secure mean?
Before we can talk about secure storage, we need to clarify what “secure” you mean. Computer science offers many storage options because everyone has different storage requirements.
- Safe from hardware failures?
- Safe from theft?
- Safe from file modification?
- Safe from espionage?
- Securely always available?
Nowadays, even smartphone manufacturers advertise secure storage, USB sticks are supposed to be indestructible and hard drives remain active for years. But how “secure” is secure?
Surviving hardware failures
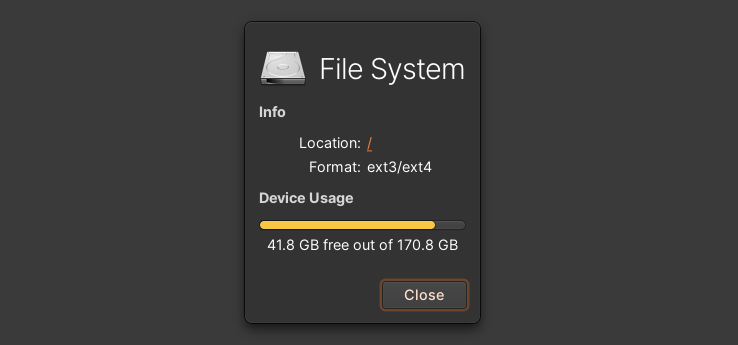
Computer hardware is not perfect.
Every technical device, with or without maintenance, breaks down sooner or later. With normal everyday objects like a coffee cup, it doesn’t matter because you can just get a new one.
Every storage device has a limited lifespan
The problem with file storage is that a broken hard drive is not replaceable (for the normal user). You want to move the data to a new device. The industry offers new devices every year that can store data more reliably and longer, but not forever.
That’s why you need a backup – a copy of your data or a RAID system. A RAID system uses multiple disks to replace the hard drive in the event of a failure. The parity bits allow one hard drive to fail and still keep the system running.
Implementation with home servers
You can buy small household boxes (home servers) where you can put 2 – 8 hard disks. If one of them fails, you can exchange the hard disk and have the RAID rebuilt.
Most secure storage against theft
Case 1: Content protection
If you just don’t want a burglar to walk out of the house with your data / laptop, the best protection is a backup that you store in another place (parents’ house etc.). You can encrypt the hard drive itself. Alternatively, you need to upgrade your doors and windows and move to a guarded house / neighbourhood.
Case 2: Luxury hardware
You have bought the fastest, best, most expensive and biggest memory bar money can buy. Now you are afraid that someone will steal it from you. In this case, a data centre operator will help you.
There you can safely lock up your system (with other expensive components) and connect it to the internet. The operator checks who go in and out and has installed security doors and cameras everywhere.
Full-scale implementation
Buy a safe and upgrade your house, so the burglar doesn’t have an easy time. If you don’t want to bear the cost of the structural measures, you can outsource the task to a 3rd party, whom you must trust completely.
Monitor every change
If you have an important file at home, you want to know if any changes have been made to it. A third person may have made changes for your benefit. Instead of memorising all the documents, there are solutions from computer science that make 99.999 % of file changes visible:
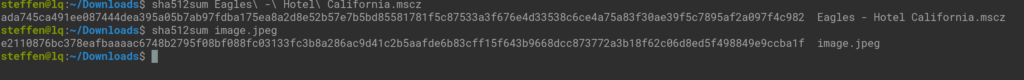
1. Hash
A hash compresses a large file to a manageable sequence of letters and numbers that is unique to each file, like a fingerprint. If you change just one letter in a 10,000-word document, the hash will change completely at least halfway through the recalculation.
Every change, no matter how small, is conspicuous. A secure algorithm is the SHA-3 512 bit in 2024, which compresses large files quickly and gives you a unique short form.
2. Versioning
Computer scientists have developed file systems and databases in which data cannot be changed, but the system always creates a new duplicate with the change.
This way you can analyse the progress of work day by day. A criminal is noticed by the fact that a new version is available and the bad guy cannot delete old versions.
3. Logging
Instead of copying every file 1000 times, the system can create a log entry when a change is made. In most cases, it is sufficient to know who changed what in which line and when.
Implementation against file changes
Cloud software like Nextcloud offers versioning. The software does not throw anything away, but saves each change individually. The timeline shows you the different version statuses per file.
Secure storage and always available?
What good is a storage facility if you can’t access it at the time of your request? If you want the storage to be accessible all year round without interruption, you need high availability.
The distributed concept
You need to have copies of your data in many locations around the world, so that in the event of a hardware failure, a local disaster (fire, flood, weather) or an attack, a copy is still available off-site. The more copies you have, the less likely it is that all copies will fail at the same time.
Cloud implementation
Cloud services offer this option. The providers make a good price for the multiple copies. You also need to add DDoS protection, because otherwise bots and criminals can overload your storage server with many pointless requests.
High security against espionage
If you as a company want to prevent your rival from getting the patent recipe for the new super drug, you have to protect your storage against espionage. What methods do I have?
In principle, you have to implement all the tips from the previous steps:
- Encryption: Documents should only be stored on fully encrypted storage devices. Any duplicate copy on a staff computer may mean that the file has already been stolen.
- Logging: You can monitor every interaction with the computer system. Logging helps you detect and prevent an intrusion. Even if the attacker was able to steal the file, you can track where the attack came from.
- Physical barriers: Spies use heavy tools to break in. You can only use heavier doors and walls that have guards watching. The more valuable the secrets, the more effort the spies put in.
- Authentication: Trust access to the protected systems only to the absolutely relevant people. Even a CEO does not need access to the recipe, only the production manager and the recipe development team.
Spy protection implementation
You should know yourself how interesting your data is for third parties. If you are developing the new super drug, you should start upgrading immediately. If you only want to protect family photos, moderate measures are sufficient. The interest of enemies (and friends) is lower here.
